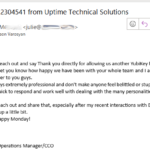
On January 10th, I received an email from a former employee some of our clients may fondly remember. The message simply read,
Subject: PAYROLL UPDATE
Hi Tyson,I want to update my new banking information before payroll is completed. What details will you need?
Regards,
James Vu
Simple right? In the midst of the January tax bustle, a business owner gets a message line this one. The sender is an employee, it is clearly addressed to me and the signature (which I omitted from this post) is spot-on. This is a common type of thing – employees change banks for various reasons… exempt for one little problem:
Trung (James) Vu tragically died in a motorcycle accident on Highway 599 back in the summer of 2020.
Taking a closer look, as one should with any email of this nature, I quickly noticed that it came from a gmail address I’d never known James to use. The person trying to impersonate him, went through the trouble of registering a new address, activating it with a phone number, and changing that account’s demographic information to match James’ name. They also copied his company signature to the letter. So they went through a bit of trouble and had more than the usual blind stab in the dark – the kind of emails we’ve seen from a “Bob” or “Adam in accounting” asking for sensitive information. Here they somewhat convincingly impersonated a real former UTS employee. How?
The answer is quite simple – someone James had emailed using his work address, had their email box compromised and his information was misused to impersonate him. Nearly always, this is a result of the recipient having an easy-to-guess password. And given as modern password-cracking rigs are becoming faster and faster, most user-set passwords are in fact very-easy-to-guess. And someone’s mailbox got hacked. Their emails were extracted and you can figure out the rest. The hackers likely trolled the hacked mailbox for other more sensitive information, but this attempt is by far he most basic way to misuse stolen email information.
The solution? As a sender, there is not one. You have to trust that people you send email to, protect their accounts. And for the recipient, that is not hard to do with 2FA or MFA, which is now available free of charge from most business email providers. It takes a bit of tech time to set it up and works by identifying and pre-authenticating devices that have connected to your email in the past. That means that you will not be prompted for a code every time you go to check your email – everything will work as it did before. However, let’s say you get a new computer, or you bought the latest iPhone want to get your email there. After the username and password, a second factor of authentication will be needed: The email provider will send a text message with a code to a cellular number that your techs pre-associated with your account and only by using that code will a new device be allowed on the “trusted” list. The inconvenience of one text code can stop these kinds of attacks dead in their tracks.
As with most security, it is not complicated, nor is it prohibitively expensive.
Identity theft however, is the biggest crime in America:
- 49 million victims in the US reported for 2021 (last year with available data).
- 5.7 million separate cases reported to the FTC 2021.
- $56 billion in total losses for 2021, to identity theft.