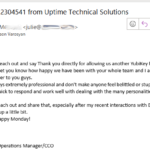
On a cold February Friday we received an alert from an established customer letting us know that someone tried to hack them! The hackers emailed a staff member who’d just started with the company a few days earlier. Representing themselves as the business owner in an email, they demanded:
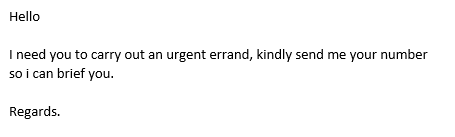
It just so happened that the owner was out of town on vacation and the employee, Tom, replied with his cell number. A few moments later, Tom got a text message stating that he was in a jam, had an urgent deadline and something that he needed on his computer and would helpful Tom be able to walk over there and help him remote in? Luckily, Tom didn’t have the user right necessary to log onto his boss’ computer and by this time he sensed that something might not be right, so he approached his immediate supervisor, who referred to a handout from a staff training we conducted there last year on how to detect fraudulent emails. He then immidiately contacted UTS.
Marc and Hamda followed our standard procedures to ensure that everything we were told was accurate. People sometimes have the tendency to omit certain truths which they fear will get them in trouble, so they verified that indeed no remote logons were made on any of the PCs within the timeline in question. Our next procedure is to freeze and preserve any evidence – the email in question was captured, Tom was instructed on how to take screenshots of the text messages and send those in for analysis.
By this time the owner’s alarmed wife contacted Tyson with concerns about how could the hackers possibly learn that Tom was a new employee and to target him like this?
Following the trail where it lead:
- The original email was very obviously bogus. It came from an @gmail.com address that clearly didn’t match the person it was trying to represent.
- The signature in the email was very simplistic and not at all correct. But the new employee didn’t really have the opportunity to know what correct emails ought to look like.
- The phone number was a bogus online texting service – anonymous. And the wildly out-of-area code, ought to raised concerns as well.
- On a hunch, we checked the server-side email rejection list (bounce list) and found that earlier that day, there were a bunch of emails bounced that were aimed at invalid addresses at the customer’s domain. All bounces were sent to addresses with common names: joe@…, peter@…, tom@… and so on.
In short, these would-be hackers got the owner’s name from the customer’s public website and shot a bunch of those emails to addresses at the customer’s domain with easy to guess names like Joe, Peter, Tom, Ana, and so on. It just so happened that a Tom started a new job there earlier that week and was gullible enough to reply with his cell number…
The lessons here are:
- Having regular staff training sessions about computer security, pays off.
- Setting emails that use common names like tom@customer.com, makes it easy not only for hackers, but also spammers to send you junk-mail that can ruin your day.
- Restrictions aimed at protecting users from themselves are a good thing. Many business have policies where everyone knows everyone’s passwords and can log in and do whatever they want…
- Procedures established from experience and ahead of time, facilitate rapid response and resolution.